Securing Data Retrieval for Decentralized Disruption- Tolerant Military Networks (DTNs) using Cipher text- Policy Attribute-Based Encryption
Securing Data Retrieval for Decentralized Disruption- Tolerant Military Networks (DTNs) using Cipher text- Policy Attribute-Based Encryption
Abstract:
DTN technologies are fast becoming popular and successful solutions in military applications that permit or enable wireless devices in the network to communicate with each other and access confidential data infallible or in a trustworthy manner by utilizing the storage nodes. However, the problem of applying CP-ABE in decentralized DTNs introduces several security and privacy challenges concerning attribute revocation, key escrow, and coordination of attributes issued from different authorities. The ABE scheme provides an access controls mechanism over encrypted data with its policies and attributes over private and masters keys, and ciphertexts (CP-ABE). Scalability is provided by CP-ABE for data encryption and decryption. For decryption to take place, the decryptor must possess attributes that match or correspond with the one defined by the security policy of the access control. We show how to apply the proposed scheme in securing and effectively manage the confidential data distribution in the DTN network.
KEYWORDS:- Access control, attribute-based encryption (ABE), disruption-tolerant network (DTN), secure data retrieval.
I. Introduction:
The military environment is a hostile and turbulent one therefore, applications running in this environment need more security to protect their data, access control, and their cryptographic methods. For communication to take place a node must be created and a connection established between the node and the neighbor nodes in this hostile networking environment, but if there is no connection between the source and the destination the message from the source node may have to wait depending on when the connection will be eventually established. We refer to this DTN architecture where multiple authorities issue and manage their own attribute keys independently as a decentralized DTN. In this paper, we describe a CP-ABE-based encryption scheme that provides fine-grained access control. In a CP-ABE scheme, each user is associated with a set of attributes based on which the user's private key is generated. Contents are encrypted under an access policy such that only those users whose attributes match the access policy can decrypt.
The concept of attribute-based encryption (ABE) is a promising approach that fulfills the requirements for secure data retrieval in DTNs. ABE features a mechanism that enables access control over encrypted data using access policies and ascribed attributes among private keys and ciphertexts. Especially, ciphertext-policy ABE (CP-ABE) provides a scalable way of encrypting data such that the encryptor defines the attribute set that the decryptor needs to possess to decrypt the ciphertext. In CP-ABE, the key authority generates private keys of users by applying the authority’s master secret keys to users’ associated set of attributes. The key authorities are semi-trusted, they should be deterred from accessing plaintext of the data in the storage node; meanwhile, they should be still able to issue secret keys to users. If the key authority is compromised by adversaries when deployed in hostile environments, this could be a potential threat to the data confidentiality or privacy especially when the data is highly sensitive. To realize the goals of CP-ABE, the key authority makes use of maters secret keys and private keys of which the users apply by requesting from the key authority. When a user keyed in some attributes that match or correspond with the one in the access policy, it is updated to match with the group attributes which provides security for group members.
II. Related Works
The concept of attribute-based encryption (ABE) is a promising approach that fulfils the requirements for secure data retrieval in DTNs. ABE features a mechanism that enables access control over encrypted data using access policies and ascribed attributes among private keys and ciphertexts. The problem of applying the ABE to DTNs introduces several security and privacy challenges. Since some users may change their associated attributes at some point (for example, moving their region), or some private keys might be compromised, key revocation (or update) for each attribute is necessary to make systems secure. This implies that revocation of any attribute or any single user in an attribute group would affect the other users in the group. For example, if a user joins or leaves an attribute group, the associated attribute key should be changed and redistributed to all the other members in the same group for backward or forward secrecy. It may result in a bottleneck during a rekeying procedure, or security degradation due to the windows of vulnerability if the previous attribute key is not updated immediately.
II. Problem Definition:
Attribute-Based Encryption poses some security and privacy problems to Disruption-Tolerant networks (DTNs). Because users in the network may change their associated attributes, master or private keys might be compromised. Therefore, to provide a secure system, the key update is very necessary, but using the ABE system the issue of a secure system is more complex and difficult since some attributes of each user are shared by multiple users in the network. This implies that revocation of any attribute or any single user in an attribute group would affect the other users in the group. The main disadvantages of this approach are efficiency and expressiveness of access.
IV. Existing System:
In the existing system, the coordination of attributes is issued from different authorities. When multiple authorities manage and issue attribute keys to users independently with their own master secrets, it is very hard to define fine-grained access policies over attributes issued from different authorities. The problem of applying the ABE to DTNs introduces several security and privacy challenges. Since some users may change their associated attributes at some point, or some private keys might be compromised, key revocation for each attribute is necessary to make systems secure. However, this issue is even more difficult, especially in ABE systems.
Disadvantages of Existing System:
1. None of the authorities can determine the whole key components of users individually.
2. Failed to issue key in decentralized.
V. Proposed System:
In this paper, we propose securing decentralized disruption-tolerant military networks (DTNs) using ciphertext-policy attribute-based encryption (CP-ABE). The proposed scheme The ABE scheme provides access controls mechanism over encrypted data with its policies and attributes over private and master keys, and ciphertexts (CP-ABE). Scalability is provided by CP-ABE for data encryption and decryption. ABE enhances the backward/forward secrecy of confidential data by reducing the windows of vulnerability. Encryptors can define a fine-grained access policy using any monotone access structure under attributes issued from any chosen set of authorities... We show how to apply the proposed scheme in securing and effectively manage the confidential data distribution in the DTN network.
Advantages of Proposed System:
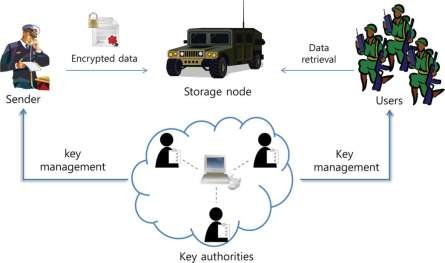
System architecture:
1. vulnerability is minimized or reduced.
2. The Key Authority exploits the characteristic of the decentralized DTN architecture.
3. When once the new attributes of the group are updated the user cannot decrypt the nodes any
4. It provides scalability for data encryption and decryption.








No comments